Lightstream Acquires Arsenal.gg, a Live Streaming Analytics Platform That Delivers Free Tools for Video Game Streamers
The platform also offers robust analytics tools for game publishers, developers, and brands to properly evaluate and intelligently build their influencer marketing strategy.
CHICAGO, March 14, 2019 – Lightstream, an innovator in live streaming technology, today announced that it has acquired Arsenal.gg, the industry-leading discovery and analytics tool for live video game streaming content. Lightstream delivers innovative, creative broadcasting technology and products that empower storytellers and address the biggest challenges streamers and content creators face.
Arsenal’s discovery and analytics tools serve two connected audiences: video game streamers and video game publishers, studio, or brands.
- Streamers utilize Arsenal’s free broadcaster profile to easily view, understand and learn how their content is performing and insights to identify and grow their audience.
- Game publishers, studios, and brands pay for Arsenal’s authoritative platform of tools to effectively build their influencer marketing strategies.
“We started Lightstream to simplify that first step in the creative journey by making streaming easier,” said Stu Grubbs, Lightstream CEO. “The second step is learning to identify and grow your audience. With the acquisition of Arsenal, we begin to help content creators optimize their stream, understand their audience, and what content is working for their channel. Arsenal is the only intuitive analytics platform that delivers its data in a smart, easy-to-understand way so that brands and streamers can really put the information to work.”
World-class game publishers, indie game developers, and brand leaders are among Arsenal’s impressive roster of industry clients and include PUBG Corp, 505 Games, and Discord.
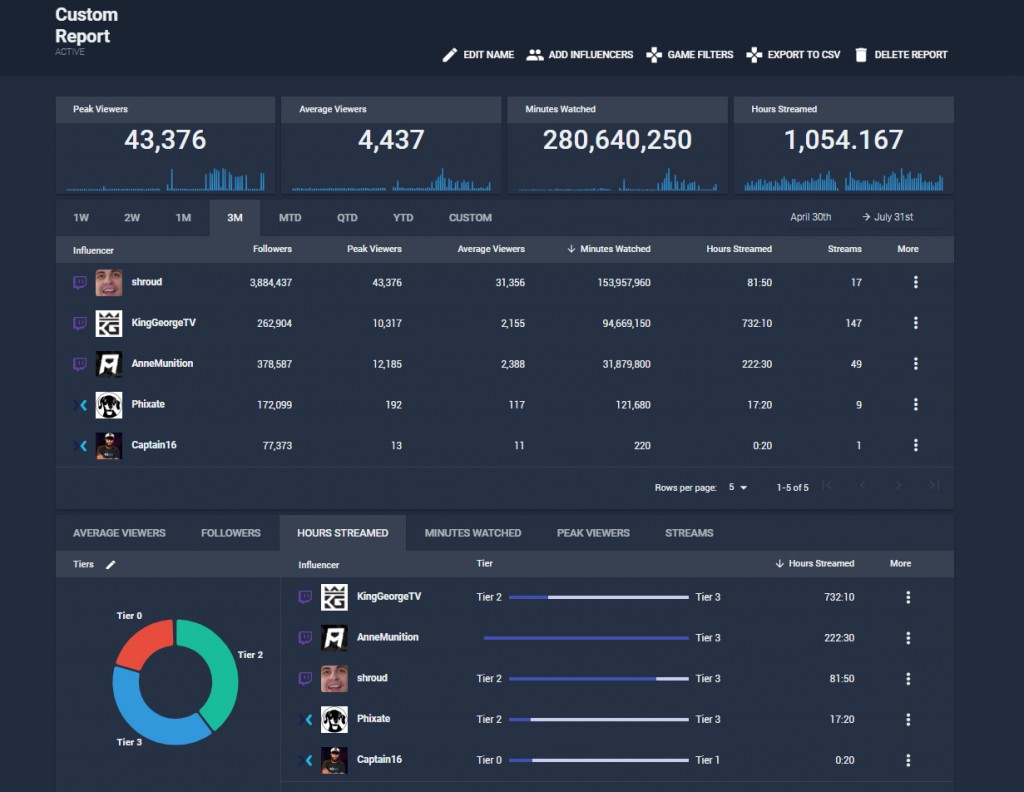
These clients have access to data across thousands of games and millions of broadcasters. They can search across over 7.5 Million broadcasters by games played, language, affiliation, or popularity across the six most popular streaming platforms – Mixer, Twitch, Facebook, YouTube, Mobcrush, and Smashcast.
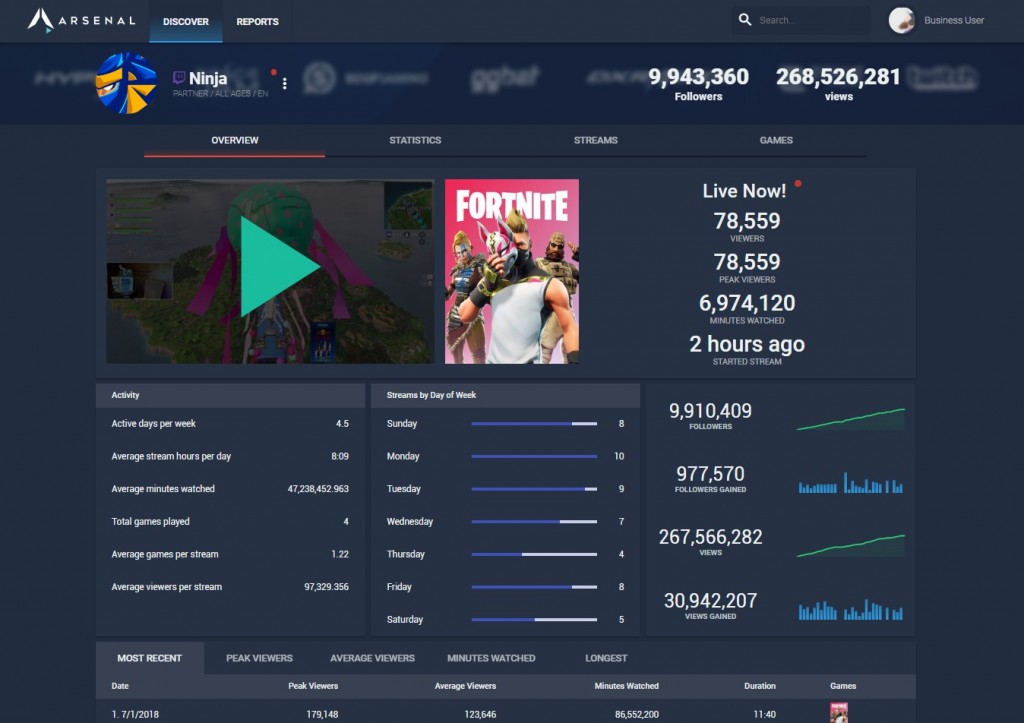
Arsenal’s streamer analysis can incorporate: broadcast details with breakdowns by game, usual time and day of broadcasts, growth and viewership metrics, active days per week, and averages of stream hours by day, minutes watched and viewers per broadcast.

“The majority of the industry is operating out of spreadsheets and self-reported data. This doesn’t scale and leads to huge inaccuracies that serve only to hurt brands and streamers. Wasted dollars or inaccurate data will only reduce the confidence level in this channel for brands,” continued Stu Grubbs. “Arsenal gives brands the accurate data they need to keep investing more of their budget in broadcasters and the livestreaming market. We’re proud to add this fantastic product and bright team to our Lightstream crew.”
For more information and to sign-up for Arsenal’s free analytics platform please visit, https://arsenal.gg. Be sure to follow @Lightstream on Twitter and at https://golightstream.com.
GDC
For brands and developers interested in meeting with Lightstream about the Arsenal platform during GDC, please reach out to Reed Scarfino at reed@golightstream.com or Jeff Royle at jeff@golightstream.com.
About Lightstream
Lightstream is a Chicago-based startup built with a true passion for live video production, gaming and supporting the explosive growth of creators and their communities. Its cloud-based technology and products transform difficult technical hurdles into streamlined workflows. Lightstream empowers creators to effortlessly share their passion, talent, and creativity on live streaming platforms like Mixer, Twitch, Facebook, YouTube and more.
golightstream.com
About Arsenal.gg
Arsenal.gg is a live streaming data and analytics platform. For individual creators, it delivers free performance statistics and insights to grow their channels. Arsenal also offers an authoritative paid platform for game publishers, studios, and brands to accurately identify viewership trends across the ecosystem as well as discover, build, and track influencer marketing strategies.
arsenal.gg
# # #
Contacts:
Tori Beebe, Lightstream PR
tori@golightstream.com
Wendy Knowles, Lightstream PR
wendy@golightstream.com




